bash-3.00# cp openssl-ECprime256v1.cnf openssl-ECprime256v1_CLIENT.cnf
bash-3.00# vi /usr/local/ssl/openssl-ECprime256v1_CLIENT.cnf
[ CA_default ]
stateOrProvinceName = optional
↓
#stateOrProvinceName = optional
[ usr_cert ]
default_days = 3650
↓
default_days = 1825
# keyUsage = nonRepudiation, digitalSignature, keyEncipherment
↓
keyUsage = critical,digitalSignature, keyEncipherment
nsComment = "OpenSSL Generated Certificate"
↓
#nsComment = "OpenSSL Generated Certificate"
extendedKeyUsage = serverAuth, clientAuth
bash-3.00# SSLEAY_CONFIG="-config /usr/local/ssl/openssl-ECprime256v1_CLIENT.cnf"
bash-3.00# export SSLEAY_CONFIG
bash-3.00# openssl ecparam -genkey -name prime256v1 -out /usr/local/ssl/ECprime256v1CA/private/sol10-ut-vpn.key
bash-3.00# openssl req -new -key /usr/local/ssl/ECprime256v1/private/sol10-ut-vpn.key -out /usr/local/ssl/ECprime256v1/sol10-ut-vpn.csr -config /usr/local/ssl/openssl-ECprime256v1_CLIENT.cnf
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:jp
Organization Name (eg, company) [Internet Widgits Pty Ltd]:openam
Organizational Unit Name (eg, section) []:openam.net
Common Name (e.g. server FQDN or YOUR name) []:sol10-ut-vpn
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
bash-3.00# openssl asn1parse -in /usr/local/ssl/ECprime256v1/sol10-ut-vpn.csr
0:d=0 hl=4 l= 260 cons: SEQUENCE
4:d=1 hl=3 l= 172 cons: SEQUENCE
7:d=2 hl=2 l= 1 prim: INTEGER :00
10:d=2 hl=2 l= 74 cons: SEQUENCE
12:d=3 hl=2 l= 11 cons: SET
14:d=4 hl=2 l= 9 cons: SEQUENCE
16:d=5 hl=2 l= 3 prim: OBJECT :countryName
21:d=5 hl=2 l= 2 prim: PRINTABLESTRING :jp
25:d=3 hl=2 l= 15 cons: SET
27:d=4 hl=2 l= 13 cons: SEQUENCE
29:d=5 hl=2 l= 3 prim: OBJECT :organizationName
34:d=5 hl=2 l= 6 prim: UTF8STRING :openam
42:d=3 hl=2 l= 19 cons: SET
44:d=4 hl=2 l= 17 cons: SEQUENCE
46:d=5 hl=2 l= 3 prim: OBJECT :organizationalUnitName
51:d=5 hl=2 l= 10 prim: UTF8STRING :openam.net
63:d=3 hl=2 l= 21 cons: SET
65:d=4 hl=2 l= 19 cons: SEQUENCE
67:d=5 hl=2 l= 3 prim: OBJECT :commonName
72:d=5 hl=2 l= 12 prim: UTF8STRING :sol10-ut-vpn
86:d=2 hl=2 l= 89 cons: SEQUENCE
88:d=3 hl=2 l= 19 cons: SEQUENCE
90:d=4 hl=2 l= 7 prim: OBJECT :id-ecPublicKey
99:d=4 hl=2 l= 8 prim: OBJECT :prime256v1
109:d=3 hl=2 l= 66 prim: BIT STRING
177:d=2 hl=2 l= 0 cons: cont [ 0 ]
179:d=1 hl=2 l= 9 cons: SEQUENCE
181:d=2 hl=2 l= 7 prim: OBJECT :ecdsa-with-SHA1
190:d=1 hl=2 l= 72 prim: BIT STRING
bash-3.00# openssl ca -key /usr/local/ssl/ECprime256v1/private/sol10-ut-vpn.key -in /usr/local/ssl/ECprime256v1/sol10-ut-vpn.csr -cert ECprime256v1/cacert.pem -keyfile /usr/local/ssl/ECprime256v1/private/cakey.pem -config /usr/local/ssl/openssl-ECprime256v1_CLIENT.cnf
Using configuration from /usr/local/ssl/openssl-ECprime256v1_CLIENT.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
fc:ca:db:0a:8e:f5:ce:9f
Validity
Not Before: Apr 30 19:14:38 2012 GMT
Not After : Apr 29 19:14:38 2017 GMT
Subject:
countryName = jp
organizationName = openam
organizationalUnitName = openam.net
commonName = sol10-ut-vpn
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Subject Key Identifier:
A8:13:B3:8E:E8:23:84:E6:F6:DF:14:39:FE:F2:F6:41:FB:78:C0:6D
X509v3 Authority Key Identifier:
keyid:9C:75:4F:D2:F1:DB:B5:C7:64:C7:05:6E:A5:4B:FE:8B:F6:32:E7:26
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
Certificate is to be certified until Apr 29 19:14:38 2017 GMT (1825 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
fc:ca:db:0a:8e:f5:ce:9f
Signature Algorithm: ecdsa-with-SHA256
Issuer: C=jp, O=openam, OU=openam.net, CN=OpenSSL ECprime256v1
Validity
Not Before: Apr 30 19:14:38 2012 GMT
Not After : Apr 29 19:14:38 2017 GMT
Subject: C=jp, O=openam, OU=openam.net, CN=sol10-ut-vpn
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:bd:ca:1e:f9:d1:fb:6a:63:08:77:fb:5d:2e:4c:
df:31:3b:71:82:1e:ef:7d:2b:e8:cd:56:b7:64:71:
76:83:72:86:94:f7:f6:67:74:cd:4d:18:7d:e8:8c:
78:ec:9c:02:9a:19:62:7a:eb:10:a5:36:98:85:ac:
34:bf:a2:e7:69
ASN1 OID: prime256v1
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Subject Key Identifier:
A8:13:B3:8E:E8:23:84:E6:F6:DF:14:39:FE:F2:F6:41:FB:78:C0:6D
X509v3 Authority Key Identifier:
keyid:9C:75:4F:D2:F1:DB:B5:C7:64:C7:05:6E:A5:4B:FE:8B:F6:32:E7:26
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
Signature Algorithm: ecdsa-with-SHA256
30:44:02:20:1b:d5:0d:35:d7:42:15:9b:a7:0e:f2:3a:e5:aa:
a8:5f:66:16:27:23:4c:de:fb:29:1f:72:5f:c4:67:f6:e4:5b:
02:20:57:ae:a1:2a:c4:f9:ea:76:c2:e3:53:c8:4e:5a:32:fc:
f3:7c:36:03:1c:09:e2:5b:85:f3:91:f8:28:db:0b:63
-----BEGIN CERTIFICATE-----
MIICDjCCAbWgAwIBAgIJAPzK2wqO9c6fMAoGCCqGSM49BAMCMFIxCzAJBgNVBAYT
AmpwMQ8wDQYDVQQKDAZvcGVuYW0xEzARBgNVBAsMCm9wZW5hbS5uZXQxHTAbBgNV
BAMMFE9wZW5TU0wgRUNwcmltZTI1NnYxMB4XDTEyMDQzMDE5MTQzOFoXDTE3MDQy
OTE5MTQzOFowSjELMAkGA1UEBhMCanAxDzANBgNVBAoMBm9wZW5hbTETMBEGA1UE
CwwKb3BlbmFtLm5ldDEVMBMGA1UEAwwMc29sMTAtdXQtdnBuMFkwEwYHKoZIzj0C
AQYIKoZIzj0DAQcDQgAEvcoe+dH7amMId/tdLkzfMTtxgh7vfSvozVa3ZHF2g3KG
lPf2Z3TNTRh96Ix47JwCmhlieusQpTaYhaw0v6LnaaN8MHowCQYDVR0TBAIwADAO
BgNVHQ8BAf8EBAMCBaAwHQYDVR0OBBYEFKgTs47oI4Tm9t8UOf7y9kH7eMBtMB8G
A1UdIwQYMBaAFJx1T9Lx27XHZMcFbqVL/ov2MucmMB0GA1UdJQQWMBQGCCsGAQUF
BwMBBggrBgEFBQcDAjAKBggqhkjOPQQDAgNHADBEAiAb1Q0110IVm6cO8jrlqqhf
ZhYnI0ze+ykfcl/EZ/bkWwIgV66hKsT56nbC41PITloy/PN8NgMcCeJbhfOR+Cjb
C2M=
-----END CERTIFICATE-----
Data Base Updated
bash-3.00# cat /usr/local/ssl/ECprime256v1/private/sol10-ut-vpn.key /usr/local/ssl/ECprime256v1/newcerts/FCCADB0A8EF5CE9F.pem /usr/local/ssl/ECprime256v1/cacert.pem | openssl pkcs12 -export -out /usr/local/ssl/ECprime256v1/certs/sol10-ut-vpn.p12 -name "UT-VPN Server"
Enter Export Password:sol10-ut-vpn
Verifying - Enter Export Password:sol10-ut-vpn
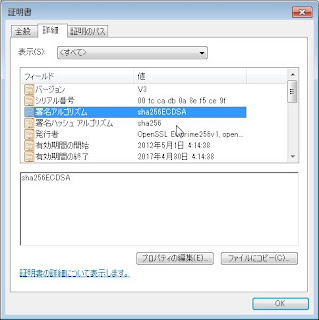
・出来上がったCA証明書(抜粋)










0 件のコメント:
コメントを投稿